Multi-Factor Authentication (MFA). Don’t make excuses, start using it now
In this tech-driven society, the internet is a part of our day-to-day lives. We use computers and mobile phones for banking, shopping, entertainment and keeping in touch with loved ones. Many of us rarely go an hour without checking Facebook, Netflix, Amazon, Instagram, WhatsApp etc. Could you imagine the damage caused if someone (or something) was to take control of these services? The impact can be devasting, both socially and financially. Wouldn’t you want to protect yourself and your family against such a thing?
It’s the same in business, it’s vital to protect your data and services from hackers. At Mintivo, we’re passionate about Cyber Security services and have a particularly important security message to share – the significance of multi-factor authentication, also referred to as MFA.
While we all might be familiar with the term two-factor authentication (2FA), MFA refers to all two-factor verification procedures which require two or more pieces of information to access a service. It may be easier to think of it like this:
MFA uses 2 elements. 1. Something you know and 2. Something you have
The problem with password-only
Passwords can fall into the wrong hands. All-to-often, passwords are re-used across many platforms and services and they’re easily guessed. That’s a big risk. MFA adds an extra layer of security to verify your identity.
Microsoft Authenticator – a simple tool for managing MFA
Microsoft account holders (that includes personal Outlook.com/Hotmail accounts as well as business users) will have access to the Microsoft Authenticator mobile application which is used to approve sign-ins using:
• Push notifications
• Biometrics
• OTP (one-time passcodes)
Additionally, the Microsoft Authenticator lets you completely scrap those hard-to-remember passwords and replace it with two-step verification (2FA) to boost the security of your accounts from your phone.
Why we recommend that you implement MFA today
Cyber-attacks occur daily and the risk of someone breaching your online security is higher than ever before. Even though we’re aware of the dangers, there are many individuals and organisations that do not implement effective security practices. 80% of data breaches come from password-only security.
In this article we want to share tips and advice to get you started with MFA to stay safe, secure, and resilient.
MFA is such a pain, should I really bother? Consider the damage if you don’t!
MFA often gets a bad reputation because it can feel like a tedious and time-consuming process, but when you consider the dangers and the impact of a security breach, it makes perfect sense. Ask yourself; what would it cost our business if our customer data was lost or stolen? What reputational damage would we suffer? How would we get work done if we can’t access our systems?
Consider this; 86% of hacking activities are financially motivated, while 70% of it is caused by outsiders and regardless of the industry you’re working in or where you find yourself (in terms of your location), you are a potential target.
And, MFA is a lot easier to implement than it once was.
The typical reasons (and excuses) for not implementing MFA
Here are some of the typical concerns that we hear regularly:
I don’t want to distract users right now so let’s do it later
That’s understandable but remember the risks and potential damage. And, it’s less disruptive than you might think. Typically, it takes our clients 5-10 minutes per user if they follow our guide.
I don’t want business apps on personal phones
Fair enough, that can be a problem. But again, consider the risks and look for ways to allow a business-orientated
authenticator app on the user’s personal phone. Consult with your users and explain the importance.
Ultimately, it’s worth a small amount of disruption for a lot more protection and future resilience, so don’t let the excuses win!
The Microsoft Authenticator app
Microsoft Authenticator is one tool in the MFA mix that provides the second ‘what you have’ element in the process. It’s an app that sits on a mobile phone to add the second layer of security.
While Microsoft’s security expert, Alex Weinert, cautions users that all authenticators are vulnerable to a breach, implementing this additional layer of security can notably reduce the risk of an attack. The authenticator can become vulnerable when exposed to a channel that’s been “jacked” – also, referred to as Channel Jacking or Real-time Phishing. Here are brief definitions of these terms:
Channel-jacking refers to the interception of a communication channel on your phone. For example, when you receive a push notification with a code to type into a login screen, your data becomes vulnerable because the mobile network, infrastructure, SIM card infrastructure is the active ‘channel’ that an attacker would use as a mechanism to take over. The most common channels used are emails, text messages as well as push notifications.
Real-time Phishing is like ‘regular’ phishing but in real-time. This refers to phishing requests that take you to a site that replicates the site it is impersonating. Real-time phishing will lead a user directly to an attacker using the Machine-in-the-middle (MitM) or “man-in-the-middle” credential interception. This often occurs when a user responds to a link received via email and takes the user to a doppelganger site that might require a password login. Doing so means that the attacker will have the user’s password and it is basically game over.
How the Microsoft Authenticator works
If your organisation isn’t already using MFA for Microsoft 365, you need to download the easy-to-use (and free) Microsoft Authenticator smart phone app.
Download and install the Microsoft Authenticator app for Android, iOS or Windows Phone.
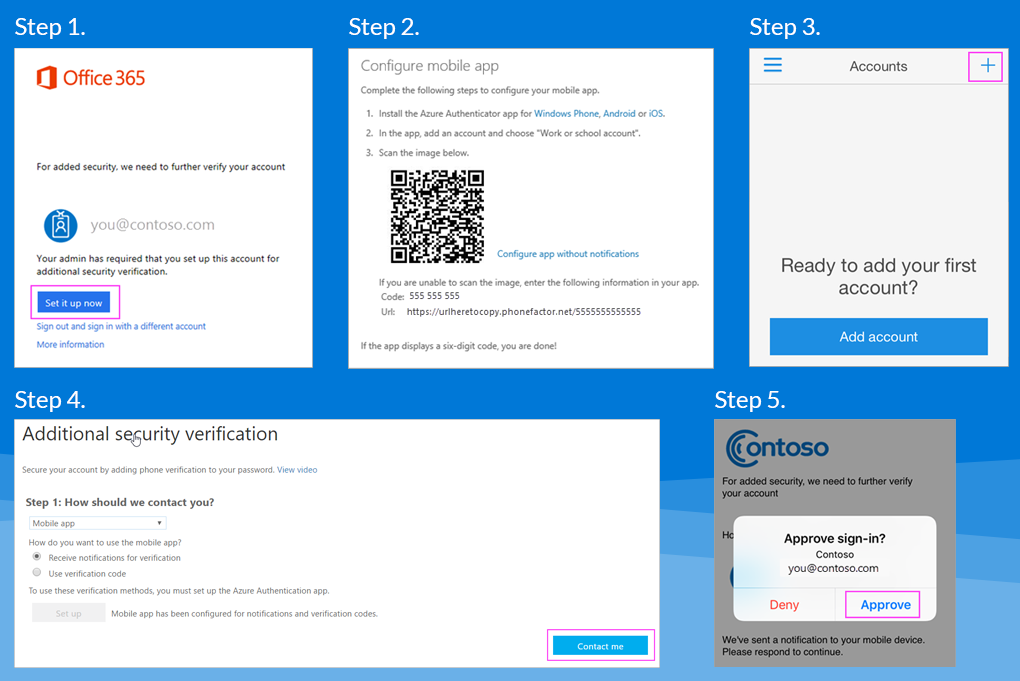
The authenticator app can be set up in 5 simple steps:
Step 1:
Once you’ve downloaded the app, it’s time to synchronise your app with your Office 365 account. Log into your Office business account, you’ll see a prompt for More information required, proceed and click Next. The next step will require you to select the method of authentication, in this case, choose Mobile App from the dropdown menu.
Step 2:
After you’ve selected your method of verification, you’ll see the question “How do you want to use the mobile app?”. You have the option to choose either Receive notifications for verification or Use a verification code. Click the Set up button to proceed with the configuration.
Step 3:
Grab your mobile phone and open the Microsoft Authenticator app. Follow the prompts to complete the wizard then click the plus (+) sign to add your business account. Choose the account you’d like to use and select Allow when prompted for permission to take pictures and recorded video. Thereafter, you’ll be able to scan the QR code on your computer to verify your device.
Step 4:
Following the account set up on your phone, tap the Got it button then go back to your computer. In the configuration window on your computer, choose Next, and then choose Next again. At this point you’ll have to enter the code on your computer that you see in the mobile app. Once you’ve entered the code, click the Verify button.
Step 5:
The final step will require you to enter a backup phone number (not the device you’re working with). When you’ve entered the number, choose Next, then click Done and you’re all set!
Tips from the pros
Over and above MFA, your accounts will need a regular passcode and Microsoft has a few tips for you (for personal and business account Cyber Security).
• Be aware that enforcing excessively long passwords will introduce other burdens (such as time taken to enter passwords, and the increased likelihood of mistyping especially on touch screen devices). Adopting the ‘three random words’ technique can help users create suitably complex passphrases that they can actually remember. See the NCSC guidelines here.
• Eliminate character-composition requirements. For example, it will become predictable when users are required to use one uppercase, one lowercase and a non-alphanumeric code because people tend to start with the uppercase letter at the beginning of the password or use numbers that mirror the shape of a letter in order to make it easy to remember.
• Eliminate mandatory periodic password resets for user accounts (people might become lazy and start using common passwords).
• Ban common passwords to keep the most vulnerable passwords out of your system.
• Educate your users not to reuse their password for non-work-related purposes.
• Enforce registration for multi-factor authentication.
• If you receive an MFA notification you’re not expecting, change your password immediately. Don’t, under any circumstances, simply authorise the authentication
There are multiple high-ranking MFA apps available to you which can help you improve your security across various apps outside of the Microsoft suite. Some of the most popular ones are Duo Security, Google Authenticator, LastPass and Authy. But, don’t forget; now that your phone has become a principal feature in the verification process, it means you’ll have to double up on your mobile phone security as well such as the use of numeric code, patterns, facial recognition or biometrics.
If you need some advice or have any concerns about your organisation’s vulnerability, give us a call on 03300 88 33 10 so that we can chat about a solution that will work for you.