
Mintivo Announces New Managing Director: Alex Jukes
We’re pleased to announce Alex Jukes as Mintivo’s new Managing Director! Alex has been an invaluable member of the team, leading our commercial arm for

We’re pleased to announce Alex Jukes as Mintivo’s new Managing Director! Alex has been an invaluable member of the team, leading our commercial arm for

What is endpoint security? Endpoint security protection is designed to form part of an organisation’s cyber security programme. Due to the increasingly sophisticated attacks taking

Terms such as assessment and audits are sometimes used interchangeably, however it is important to understand the differences. Generally speaking, an assessment is an internal

Cybercrime is on the rise. In fact, it’s estimated there were 2.39 million instances of cyber crime and approximately 49,000 instances of fraud as a

Why is email security important? Emails are one of the easiest routes for hackers to spread malware or for criminals to undertake scams. Malware can

Five years ago, online conference calls were the exception. They required expensive hardware, unwieldy software, and a good experience was not always guaranteed. The recent
With the dramatic rise in remote and hybrid working over the past few years, it’s no surprise that we’ve also seen a huge increase in

Digital transformation is the integration of digital technology into all areas of a business. Digital transformation enables you to fundamentally change how you operate to

The Microsoft 365 suite of market-leading applications is widely recognised for its ability to make our lives easier, both at the office and at home.

Users of Microsoft Windows will be familiar with the look and feel of the desktop interface they access when they first power up their local

Have you ever received a suspicious email? The kind of email that might say you’ve won some money, or maybe even an email from a

As you almost certainly know, Microsoft Entra ID, formally known as Azure Active Directory, is Microsoft’s comprehensive cloud platform, offering more than 200 products and

Patch Management is essential to your organisation’s security and productivity, but what exactly is patch management and why do you need a patch management strategy?

When it comes to choosing user collaboration tools, Microsoft Teams emerges as a powerhouse, transforming the way teams communicate and work together. This guide aims
In simple terms, network infrastructure is the combination of the software and hardware components which help build, run, and maintain an IT network. The IT

Businesses and organisations rely on the smooth running of their IT systems. But what happens when something goes wrong? As we have discussed before, it

With the need to keep on top of technological advances and better ways of doing business, cloud transformation is becoming an increasingly popular option for
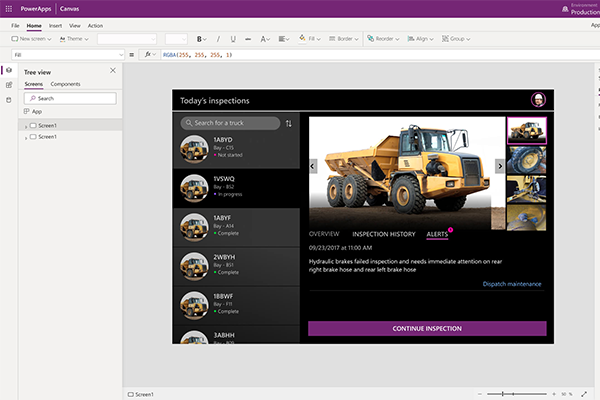
Traditionally, the route to creating a business application was long, winding, and expensive. One of the issues was how to translate the business needs of

A network security assessment is an audit or cyber security audit used to identify any potential security threats or vulnerabilities within an organisation’s IT network.

Cyber security is about protecting your data from attacks from cyber criminals. These attacks are malicious and are usually aimed at accessing and misusing confidential
03300 88 33 10
Mintivo, 1 The Sidings, Lacock Green,
Lacock, Chippenham, SN15 2NL
hello@mintivo.co.uk